According to the IBM Report: Escalating Data Breach Disruption Pushes Costs to New Highs, in 2024, data breaches cost businesses an average of $4.88 million per incident, and for healthcare organizations, that figure soared to nearly $10 million (IBM, 2024). The architecture behind your cloud communications matters more than most businesses realize, and some approaches introduce risks that aren’t immediately obvious.
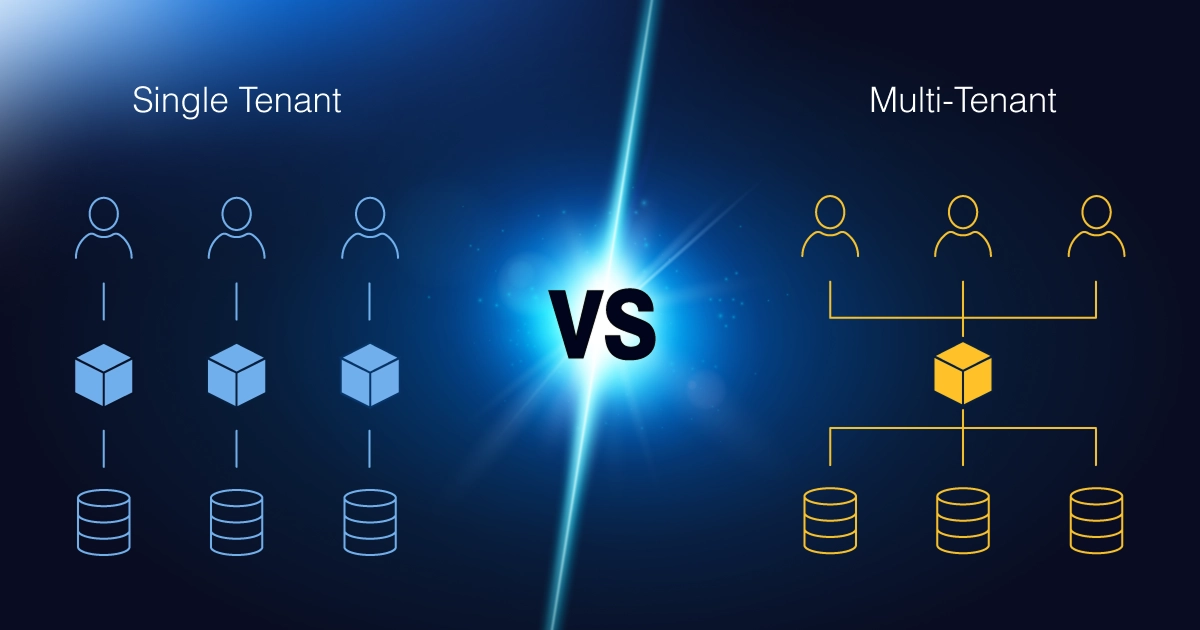
Many businesses unknowingly increase their risk by choosing cloud communications providers that rely on multi-tenant architecture. In a multi-tenant system, while tenants are logically separated, they still share the same software stack, infrastructure and control plane. A vulnerability in the shared layer can potentially expose every customer using that clustered environment.
In this post, we’ll explore single tenant vs multi-tenant security, examining why multi-tenant systems create vulnerabilities that most vendors don’t want to talk about, why regulated industries like healthcare and finance need single-tenant solutions and how hybrid deployments with survivability features ensure your communications never go down, even if the internet does. Most importantly, we’ll show you how single-tenant architecture doesn’t have to mean sacrificing scalability or flexibility.
See how Wildix can work for you today
What is Multi-Tenant Architecture?
In the cloud communications world, many vendors use what is called multi-tenant architecture. This means they place a number of different customers in the same shared environment: the same servers and the same cluster, only separating them through software.
At first glance, this setup looks cost-efficient. But it actually creates risk. When multiple businesses sit together on one shared system, a problem in the shared application layer or shared cluster resources can cascade across tenants.
There are also limits for organizations that must meet strict compliance standards. Highly regulated industries such as finance, healthcare or government organizations often cannot share their environment with other companies. Yet many vendors still offer only multi-tenant setups, giving their customers no choice.
Multi-tenant architecture is common because it reduces the vendor’s costs. But it does not always give customers the privacy, control or security they actually need. That is where a single-tenant approach starts to matter.
What Is Single-Tenant Architecture?
In a single-tenant architecture, each customer gets their own dedicated instance of the software and supporting infrastructure. Your PBX instance does not share its configuration, database or call-control environment with any other customer.
This stands in contrast to multi-tenant architecture, where numerous customers operate within the same shared environment (the same servers and the same cluster) with only logical, software-based separation between organizations.
The key advantages of single-tenant architecture include:
- Dedicated resources: You’re not competing for bandwidth, processing power or storage with other organizations.
- Enhanced security: Your PBX runs in its own private instance with its own configuration, database and call-control environment, completely separate from every other customer.
- Independent performance: Other customers’ activities or security incidents cannot impact your operations.
The Hidden Risks Vendors Don’t Want to Talk About
Understanding single-tenant vs multi-tenant security is crucial because most cloud communications vendors won’t openly discuss how their platforms are built. Many run all their customers on the same shared AWS cluster, with only software-based separation between environments. While this approach cuts infrastructure costs, it also creates a single point of failure.
Multi-tenant cloud systems depend on a single shared application layer. If that shared layer experiences a vulnerability, misconfiguration or overload, every customer in the cluster may be exposed to the same risk because all tenants rely on the same underlying stack. In a single-tenant model like Wildix’s, each customer’s PBX runs in its own isolated instance. Even if a shared service or infrastructure layer were affected, the blast radius is dramatically reduced because each PBX environment is independent. Instead of one weakness exposing an entire customer base, any impact would be contained to a single PBX instance, not an entire cluster.
And, this isn’t just a theory; it’s how large multi-tenant platforms typically work. A vulnerability in the shared layer can expose every tenant relying on that same stack. So, because customers have no visibility into who they’re sharing infrastructure with, they often don’t realise they’re inheriting risk created by other organisations, including those with weaker security practices.
In a world where cyberattacks grow more sophisticated every year, a shared environment means your security posture is only as strong as the weakest point in the shared application layer.
See how single-tenant architecture can benefit your business
Why Regulated Industries Can’t Afford Multi-Tenant Systems
The debate over single tenant vs multi-tenant security becomes even more critical for industries where data protection is non-negotiable, e.g., healthcare, finance, emergency services and government organizations. For many highly regulated environments, multi-tenant architecture isn’t just risky; it often fails to meet internal governance or regulatory requirements. These organizations need private cloud unified communications where their PBX environment is not affected by issues in a shared application layer.
Yet many major cloud communications vendors still do not offer true single-tenant, private-cloud deployment options, leaving regulated organisations to accept architectures that fail to meet their own governance or compliance requirements.
The cost of downtime in critical environments
Compliance is only part of the story. These industries also can’t afford any downtime. In a hospital, when medical staff need to communicate during a cardiac emergency, or when an emergency dispatcher needs to coordinate first responders, a communication failure could be life‑threatening.
Private cloud: Maximum control for regulated industries
For organizations with the strictest requirements, a private cloud approach offers the highest level of control. Unlike public cloud deployments, where infrastructure is shared, a private cloud means running your communications system on infrastructure you own and manage. You control the physical servers, the network, the security policies and where your data resides. This level of control is often essential for meeting specific regulatory requirements or internal governance standards.
Wildix supports this through Virtual Cloud deployment, allowing you to install the PBX as a virtual machine on your own infrastructure using platforms like VMware ESXi, Microsoft Hyper‑V or Proxmox VE. You maintain complete control over your resources and security while still connecting to Wildix cloud services for collaboration and AI capabilities.
How Wildix Delivers Single-Tenant Architecture Without Sacrificing Scalability
With Wildix, businesses don’t have to compromise. Our single-tenant model gives each customer their own environment, their own resources and an isolated PBX instance, aligning naturally with the strictest industry standards.
Our architecture doesn’t just claim to be secure; it’s been independently validated. Wildix has achieved AWS Foundational Technical Review (FTR) certification, meaning Amazon Web Services has verified that our infrastructure meets their rigorous standards for security, reliability and operational excellence. We’re also SOC 2 compliant, providing additional assurance that we maintain the highest standards for data security, availability and confidentiality. And, these certifications aren’t just badges; they’re proof that our single-tenant approach has been scrutinized and approved by independent authorities.
Traditionally, businesses believed single-tenant models were less scalable, but Wildix eliminates that limitation through its WMS Network (Wildix Management System).
WMS Network lets customers connect as many isolated systems as they want, creating a unified architecture that scales horizontally across regions and departments while preserving the security and performance benefits of true single-tenant deployments. Users, contacts and features are synchronized across the network, making it appear as a single, seamless system to the end-user, regardless of which dedicated PBX they connect to.
This means you get:
- Unlimited growth
- Seamless global expansion
- Consistent security model
- No shared PBX instance, no shared database, no shared configuration layer
It’s the flexibility of the cloud with the security of complete isolation.
Survivability by Design: Why hybrid architecture matters
Security isn’t only about keeping attackers out; it’s also about ensuring communication never goes down, even in extreme conditions.
This secure-by-design architecture approach is where Wildix’s hybrid capabilities set us apart.
Geographical flexibility for global organisations
If your business operates across continents, latency, reliability and data-sovereignty laws matter. With Wildix, each customer can choose which AWS region their dedicated instance is hosted in. This ensures better performance, compliance with regional requirements and greater resilience while maintaining the security benefits of a single-tenant deployment.
Built-in survivability and failover
For hospitals, emergency response centres, manufacturing sites and critical care facilities, downtime is not an option. Wildix offers a unique survivability model with hybrid deployment failover capabilities:
- You can deploy an on-premises PBX alongside the cloud instance.
- If the internet goes down or the cloud becomes unreachable, the on-prem system automatically takes over, keeping internal communications operational.
- Your staff can continue calling, coordinating and handling emergencies without interruption.
This is true resilience, not the ‘soft failover’ many vendors promise in shared cloud clusters.
DECT Connectivity for Mission-Critical Mobility
Inside hospitals, DECT networks ensure that nurses, doctors and critical medical staff can always reach one another. DECT’s dedicated radio signals provide superior, interference-free coverage where Wi‑Fi or cellular signals struggle due to thick walls, concrete structures, interferences or high device density. Because DECT operates on its own dedicated base stations and frequency band, it provides local communication resilience, keeping communication operational and reliable for mobile staff even when the Wi‑Fi or LTE networks are overloaded or unavailable.
This makes DECT a strategic choice for high-mobility, mission-critical environments, complementing, but separate from, the system-level failover offered by hybrid cloud deployments.
Hybrid deployments aren’t an optional extra. They’re a core part of a secure-by-design communications strategy.
Understanding Your Options: How different architectures stack up
| Architecture Type | Security Risk | Control | Isolation |
| Multi-tenant cloud | Shared software layer, shared DB, shared PBX | None | Low |
| Single-tenant cloud (Wildix Cloud PBX) | Shared AWS infra, but private PBX instance | Medium | High |
| Virtual Cloud / Private Cloud | No shared application layer, no shared cloud infrastructure. Security depends on customer’s hypervisor, network and physical protections. | High | Very High |
| On-prem appliance | No shared layers. Maximum isolation. Security depends entirely on physical security and customer environment | Highest | Highest |
Ready to Experience True Security Without Compromise?
Don’t settle for shared infrastructure that puts your business at risk. Discover how Wildix’s single-tenant architecture delivers the security, control and survivability your organization needs without sacrificing scalability or flexibility.