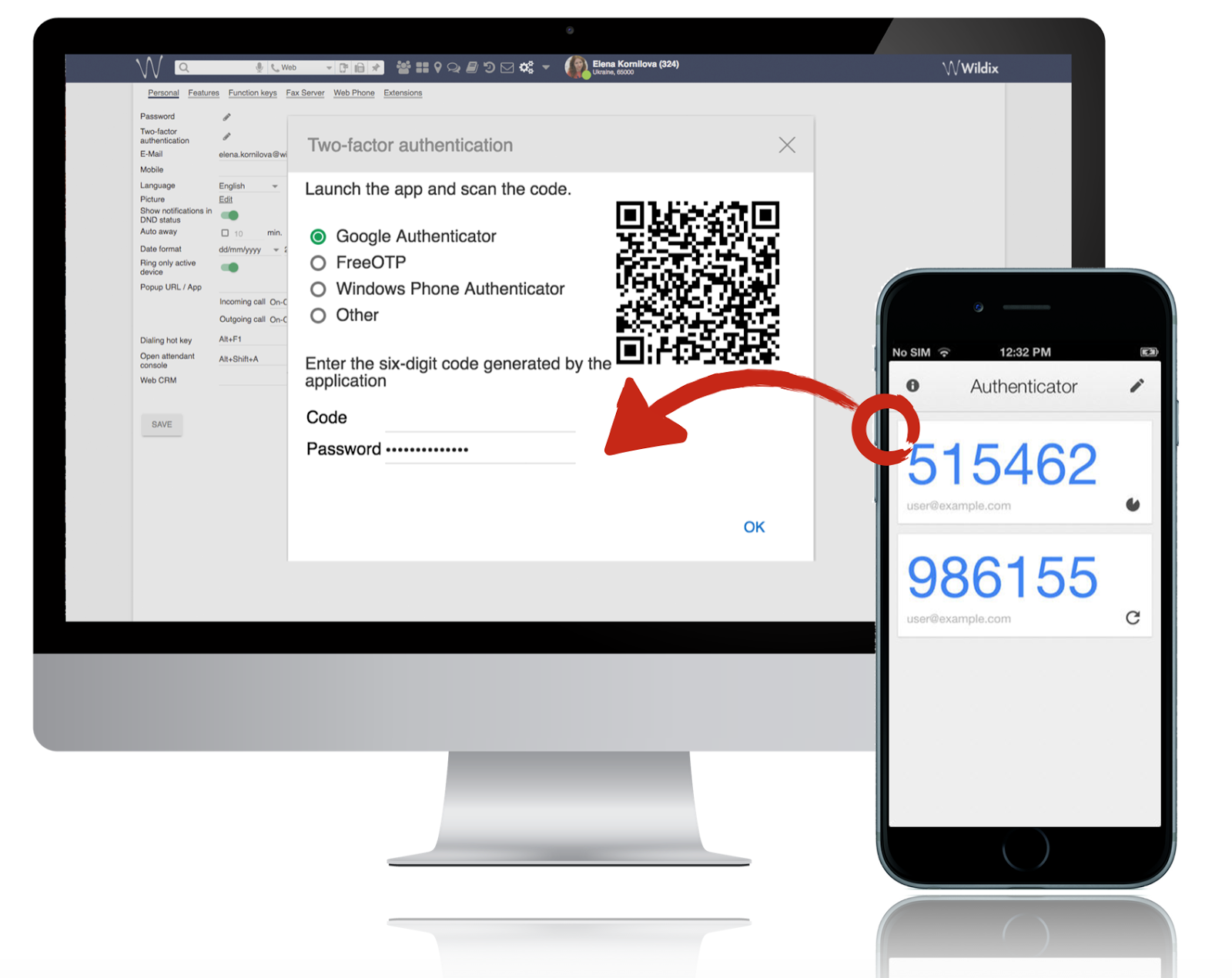
Authentication is the process in which the system identifies logged in users from unauthorized users. The effectiveness of this process is determined by the authentication protocols and mechanisms being used. In this article we will start reviewing authentication types that are used to verify the identities of users and decide whether they are really secure or not.
Basic HTTP
The first version of SIP used Basic HTTP authentication. This system is fairly easy to access using man-in-the-middle attacks. This type of authentication has been depreciating for some time now.
In HTTP authentication, an attacker can simply capture a packet containing the password and base64 encoded, which is then used to decode and perform attacks.
Not secure, indeed.