Everything you need to know about Two-Factor Authentication and why using it for UC&C services
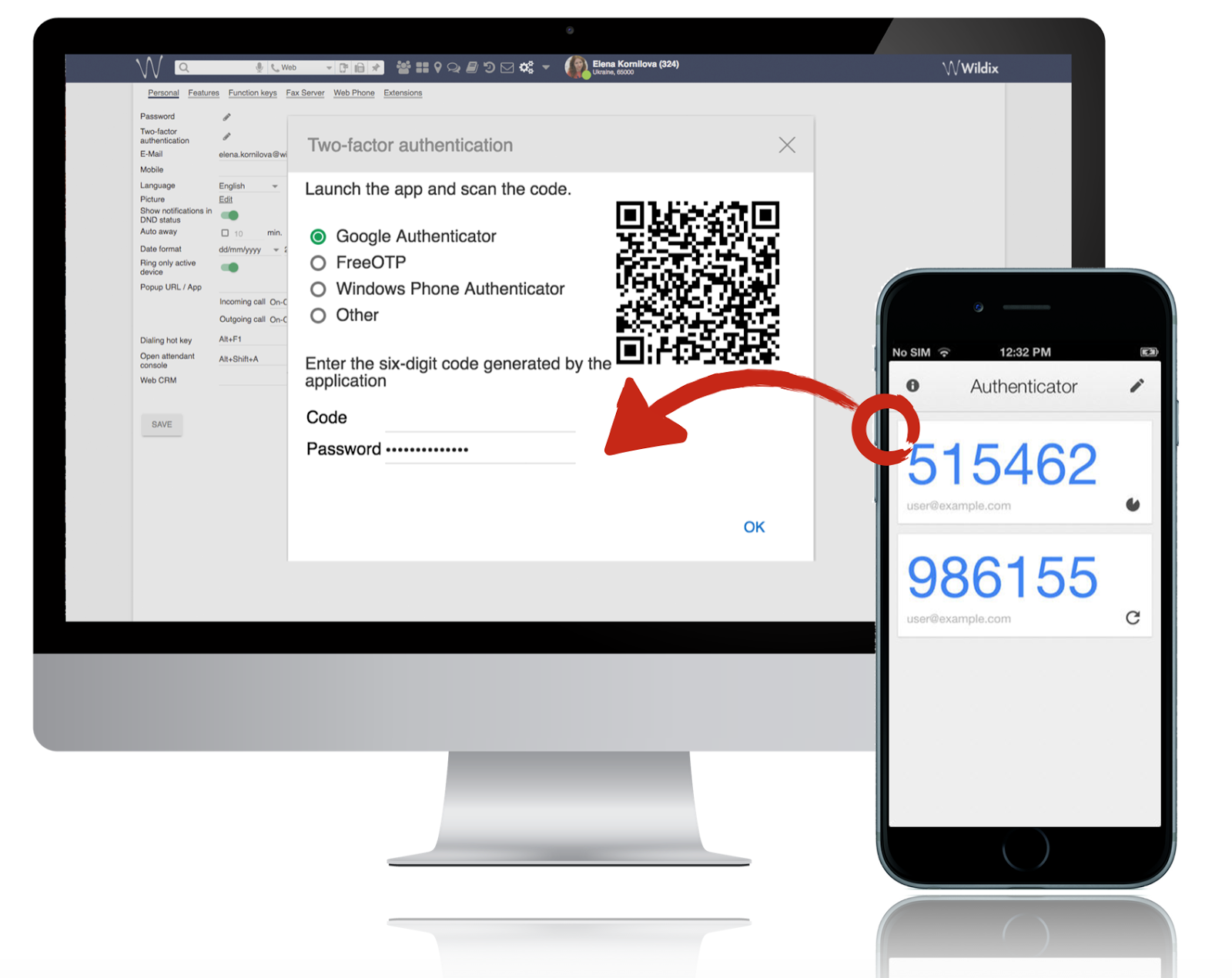
Today we use online services to shop, to collaborate, to meet new people and to keep in touch with friends. Many of these online services contain and store private information, such as user personal data, contact lists, credit card credentials, patient information etc.
However we all know that breaking into the system, in many cases, is just a question of time. Your password can be stolen or hacked every now and then.
Someone can pretend they are you and steal your identity.
In fact it has already happened to many of us at least once. What can we do to protect ourselves and our sensitive data?
Continue reading