One of the biggest strengths we talk about with Wildix is its open design and room for customization. As we like to say, you can build just about anything using our ecosystem, and the incredible use cases that Wildix partners show off prove it. But crucially, this flexibility is supported by the system being secure by design; each component of the Wildix system has built into its foundation secure principles and practices that provide automatic protection.
In all these regards, one easy comparison to make against Wildix is 3CX, a free IP PBX that went commercial in 2007. Not unlike Wildix, 3CX promises an open platform with what may appear to be significant flexibility in installation. Because the system can be used with your choice of phone number, cloud provider, hardware and even SIP trunk, it seems like a wide-open promise for building reliable systems. Even better, it promises security in its design for ready protection in deployments.
But, how well does the system hold up when you analyze it down at a detailed level? More importantly, how effective are its security protocols in practice?
In this edition of Wildix vs., we’ll consider all that and more, in particular how the two stack up with regard to usability and security.
Features & Use
It’s tempting to make further Wildix comparisons when you look at a deployed 3CX system. As a VoIP softphone, 3CX comes with the usual trappings such as:
- Voice calls
- Team messaging
- Web conferencing
- Call recording
- Screen sharing
- Mobile apps
One key point of customization comes in with 3CX’s Call Flow Designer, which allows end-users to design unique call flows for their particular system. Although the interface here is designed for simplicity, it ironically ends up holding back the possibilities for call flow options. Changing the rules for outbound calling, as one example, isn’t possible within the 3CX environment.
Still, deployment of a 3CX system is extremely simple and customizable, to an extent. Once you have your license and SIP trunk, you simply have to install 3CX over the web for either on-premise or cloud-based deployments. In this regard especially, 3CX comes close to Wildix, which can be installed by an MSP remotely in a matter of minutes.
So how does that aforementioned customization come in? Beyond your choice of SIP trunk, hardware and deployment type, 3CX is fairly easy to scale up or down through its design and unique approach to licensing (more on that later).
And after that … Well, that’s about it, actually. While 3CX does feature an “open platform” to support a wide variety of hardware and service providers, what it doesn’t feature is more ways to branch out from and build upon the existing system. Some notable integrations aside, there are a few ways to open up the 3CX system and add on to it for bespoke installations.
Compare this to Wildix, a system built for far more open customization. Wildix has significantly more call queue options, especially in that the system can be configured for custom outbound calling behavior. Thanks to numerous integrations and open APIs, Wildix can be customized even further for specific rules and functions to match an individual business’s needs. This is on top of the wealth of other call features available through additional services, such as international calling and SMS support through CLASSOUND.
While on the face of it 3CX and Wildix may appear similar in terms of usability, then, scratching past that surface reveals Wildix has significantly more to offer in terms of business capabilities.
Licensing
Earlier, we mentioned 3CX differs from many VoIP options when it comes to licensing. This is most notable in that the vendor tiers their licenses based on the number of concurrent calls a given deployment can make, not necessarily the total number of seats deployed. What’s more, the vendor promises a full year of the most basic tier for free.
3CX licensing tiers
However, the license system becomes confusing once you get down to specifics. Although there are only three plans to choose from — Standard, Pro and Enterprise — the pricing per number of extensions isn’t exactly clear from the vendor’s given sheet. In terms of planning costs, it may end up being more difficult for companies to consider future expenses if they expect an increase in users on their 3CX system.
Then there’s the free year on the Standard plan: How good a deal is this, really? Although the answer will of course depend on a given organization’s individual needs, features such as integrations for Office 365 and CRMs, custom queues, call traffic reports and call recording are available only in Pro and up. Furthermore, only 3CX Enterprise users have access to built-in failover and stand-by licenses.
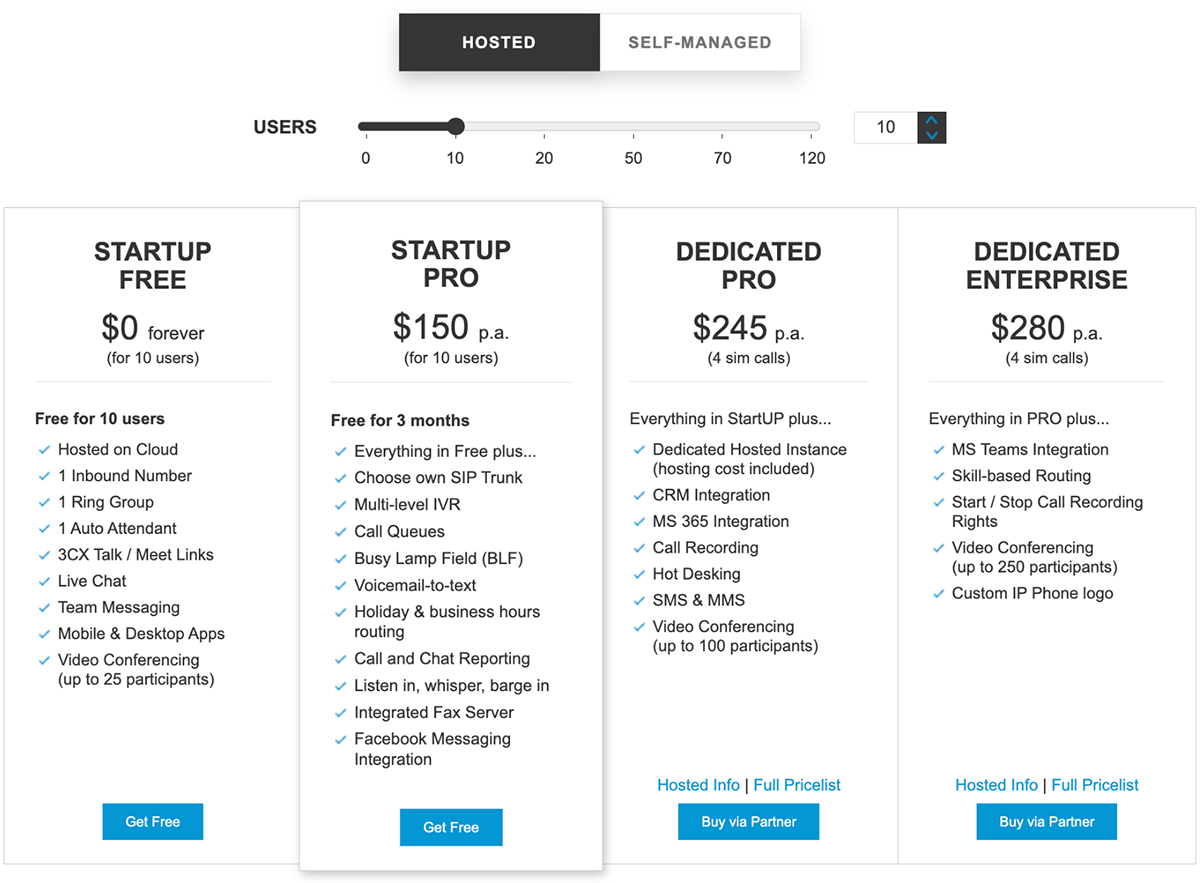
Although no free tier exists with Wildix, the licensing with this system is more straightforward and based on per-seat pricing. This tiered system is based on providing essential capabilities to more users and more advanced capabilities only as needed.
Wildix licenses
Notably, this allows for simpler mixing and matching of license types. For example, phones in a contact center can each run on a UC-Essential license, while UC-Business and UC-Premium licenses are bought only for management and C-suite personnel. This makes for more customization in terms of deployment and better ensures end-users only pay for what they need on a per-user basis.
Security
But then we come to the question of security: Are both of these systems truly secure by design? In Wildix’s case, there’s extensive documentation on how the PBX enforces security protocols right from installation and in any given deployment. Notably, Wildix uses built-in encryption methods (SRTP and DTLS in particular) to keep all communications unreadable to would-be eavesdroppers. This is in addition to building the system around WebRTC technology, which uses further encryption and direct browser-to-browser communication for fewer points of failure.
In fact, Wildix reduces points of failure even further by enforcing security without the need for VPNs or external SBCs — both of which need to be tested, updated, verified and merged successfully with a PBX to function properly, complicating the security setup and introducing more points where hackers can break in.
When researching the security for 3CX, there are many similar promises about security. Plenty of distributors describe the system as being secure on its own — and, sure enough, the system does feature TLS and Secure RTP encryption on communications.
However, unlike Wildix, 3CX recommends the use of an external SBC to secure the system. Again, this is more of a problem than initially apparent because external security measures represent a potential point of failure in a system: if that additional device isn’t configured properly, misses an update or otherwise is out of step with the main system, it can become a way for hackers to break into. As such, requiring it for full security is unwieldy at best and a security risk at worst. 3CX users can however choose to do without by provisioning phones in STUN and having some strict firewalling rules on both ends.
That’s far from the only risk 3CX appears to have had issues with, however. Perhaps more concerningly, the system has had its fair share of vulnerabilities, each of which could result in a breach.
3CX Vulnerabilities
It should first be said that vulnerabilities for software represent highly specific and, in general, fairly unlikely ways for hackers to break in. These aren’t gaping holes in the system’s armor but small cracks that, if operated on in just the right way, can nonetheless bust access wide open.
Fortunately, this also makes them easy to patch, as 3CX generally has done. But the cracks are still points of entry for hackers, and the extent that they seem to pop up mars the idea that the system is secure on its own.
One of the biggest such vulnerabilities is classified as CVE-2022-28005. In a nutshell, this vulnerability allowed hackers to break into seemingly unimportant files within the 3CX installation and, from there, take control over the entire 3CX system or even the entire computer. This vulnerability was fortunately patched out with a simple hotfix, meaning that users simply have to update their system to the latest version to avoid this issue. However, the fact that such a severe breach was possible suggests complications and vulnerabilities within the design of the system.
An additional potential for breaches exists with CVE-2019-9971 and CVE-2019-9972. Used together, these two allow an admin with a valid system login to bypass system restrictions and then escalate their access privileges — in effect giving any user accessing the 3CX system unlimited control over it. A patch has been issued for CVE-2019-9972, and it doesn’t affect users running on the Debian 10 version of the 3CX system.
Even the encryption methods from 3CX do not appear consistently applied. An additional vulnerability, CVE-2021-45490, outright caused certain installations of 3CX to not perform proper certificate verification for TLS encryption procedures. Effectively, this oversight mitigates the purpose of TLS encryption altogether.
Again, it must be reiterated that these are vulnerabilities, meaning they represent temporary and generally hard-to-access breaches in the system. But given their number and severity, it’s worth considering that they will be a component of most any given 3CX installation until they are patched out.
Support
As valuable as security is, it’s also critical to consider what happens when a system breaks down in some way.
In this regard, Wildix consistently relegates support to certified partners, who are trained in the system and have constant access to Wildix’s tech support through a 24/7 network operations center. This is in addition to the Wildix Tech Wizards page, where partners can consult with one another about system design and technical knowledge.
3CX has a similar approach to support, using a mix of instructor-led support and training videos.
Overall Value
As a whole, 3CX offers similar features to Wildix on the surface, but in the hands of a capable MSP Wildix is open to far more customization. Although 3CX allows users to bring their own SIP trunk, cloud provider and connecting hardware, the actual capabilities and use cases it provides are fairly limited. Wildix, in contrast, has significantly more potential for bespoke design to fit individual customer needs.
Licensing is more complicated under 3CX, and although a free year is available under one tier, many significant capabilities are missing from this trial. It’s difficult to compare Wildix and 3CX purely in terms of price, as Wildix price lists are not public, but it’s worth considering that Wildix licensing allows for higher-tier features to be bought only for a few select employees (such as management and leadership).
Finally, although 3CX provides built-in security, its promises of an innately secure system are complicated by the need for an external SBC and a history of critical vulnerabilities (none of which is helped by a paid tech support ticketing system). On the other hand, Wildix provides total protection without external SBCs, and the system has little to no history of such significant security breaches.
For simpler security and far more flexibility in deployment, the choice in this matchup is quite clear.
Breakdown
| Wildix | 3CX | |
| VoIP features |
|
|
| Collaboration tool features |
|
|
| Integrations |
|
|
| Licensing | 4 licenses total, based on number of users | 3 licenses total, based primarily on number of concurrent calls |
| Support | Available through certified Partners, who have 24/7 access to Wildix experts | Available through 3CX partners or directly through 3CX for $75 USD per ticket |