How can someone compare software vendors and their effectiveness?
Are they a good vendor? If so, how do they “become” good? I could ramble on about SDLC (software development life cycles), Agile methodology, blah blah blah, but the truth is…partners don’t care about this.
What does a partner care about? Partners care that a vendor helps them drive more revenue and more profit for the long term health of their business. Or at least that is what they should care about.
So, what a partner wants is simple! A system that can be sold for a lot, installed and maintained with no effort, allows them to maintain control of their customer base and is FREE! Ah, such a blissful world! Continue reading “Is Wildix a good vendor?”
 In the
In the 

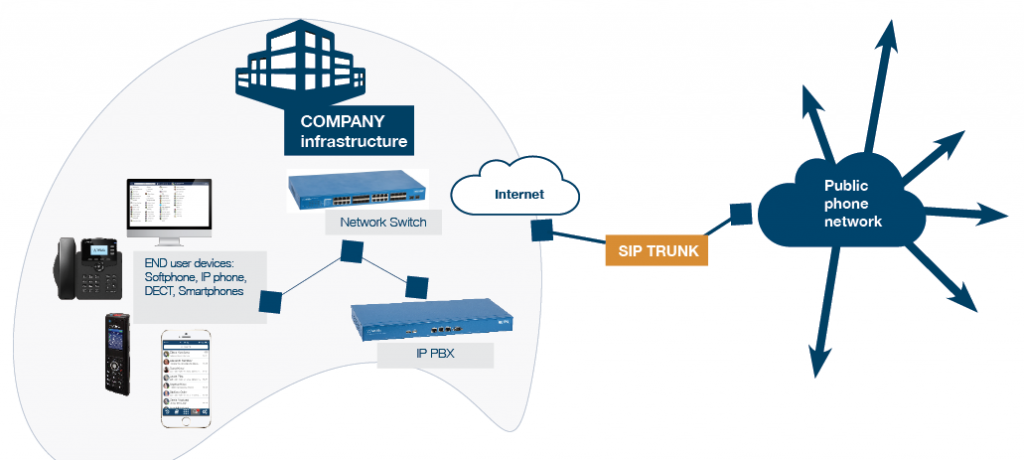 SIP Trunking
SIP Trunking