 On the internet, fraud comes in many forms. From suspicious “special offers” all the way up to royalty of dubious origin, scams are so common for online users that plenty have become woven into the folklore of the world wide web.
On the internet, fraud comes in many forms. From suspicious “special offers” all the way up to royalty of dubious origin, scams are so common for online users that plenty have become woven into the folklore of the world wide web.
Despite all that, however, cyberattackers still lurk online, eager to make good on any combination of trust, fear or just outright ignorance. Often, these bad agents are successful not because they directly penetrate system security but because they can pull off one frighteningly common hoax.
That hoax is “phishing”: one of the oddest words you’ll see in cybersecurity, even though what it represents is entirely serious.
First Steps into the Water
In a nutshell, phishing refers to a form of digital fraud where a cyberattacker tries to trick someone into revealing confidential information. The information cyberattackers look for may vary, but will tend to be login credentials or financial information.
Typically, this is attempted via an email or other message that claims to be someone important — such as a bank associate, a web technician or maybe a high-profile customer. That message is the “bait” in the situation, priming a digital hook for targets to latch onto and then be reeled in by the attacker.
The results of phishing are unsurprisingly dire, potentially costing victims access to systems, confidential data or entire financial accounts’ worth of funds. It should therefore be no surprise that some of the most successful cybercriminals in history typically make use of phishing, such as the Russian state-sponsored Cozy Bear or Fancy Bear groups.
There are several related forms of cyberattack these malicious agents can use:
- Spear phishing is where an attacker targets a specific individual (often someone with high security clearance for an online system) like a hunter spearing one specific fish
- Vishing, made up by combining “voice” and “phishing,” means a phone call where the caller falsely poses as a legitimate entity.
- Smishing, created by combining the words “SMS” and “phishing,” means text messages that pass themselves off as being from official sources.
Recognizing a Scam
So, how exactly do you defend yourself against any of these scams?
To start, the unfortunate truth is no amount of technology can protect you from any form of “-ishing.” This is because they’re all conducted through communication — not via a system intrusion. In other words, since all these scams are effectively knocking at your door, the only way to restrict their access would be to restrict every other visitor’s access as well.
With that in mind, the best way to outsmart these scammers is to recognize them. Fortunately, it often takes just a few identifiers to know which messages are fakes.
1. Beware of Urgency
Though some attackers will work patiently, most phishers tend to be impatient. Often, they’ll launch into asking for information right away with an urgent and demanding tone.
That urgency is your dead giveaway. Remember, a legitimate IT professional or financial agent would never rush you into giving away sensitive information, let alone over electronic channels.
When a message tells you to give away your sensitive info right this second, odds are pretty good the reason they’re so insistent is they’re scammers out for a quick buck.
2. If It Sounds Too Good to Be True…
A surprise cash offer? A big prize for a contest you never entered? Half off from your electric bill instantly? Supposed “special offers” like these pop up again and again across phones and email inboxes.
The reason why, of course, is because they’re almost unilaterally bull.
As the old saying goes, deals that sound too good to be true almost always aren’t. So if a supposedly life-changing opportunity lands in your lap through a call, text or email, be warned it’s very likely a scammer at work.
3. Uncanny Identities
Something phishers do quite well is making their messages look authentic, down to logos or the email address.
On closer inspection, though, these disguises usually turn out to be paper-thin.
In the case of email, even when a scammer uses an official logo or business name, they typically leave in telltale signs of their dishonesty. For instance, a phisher might use an address like “home.spotify.xyz” when an actual email from Spotify would use the proper domain of “spotify.com.”
There’s also this example of an actual scam provided by the FTC:
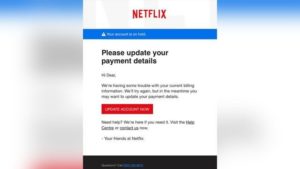
It seems authentic enough, but take a closer look at its first line: “Hi Dear”? Quite an odd way to start an account reset email, given that Netflix would normally use your name. Inconsistencies like that, small as they may seem, are essential for telling real communications from fakes.
On phone calls, meanwhile, obvious tells are when a pre-recorded message says they’re from a governmental body, or when the caller claims to represent a conveniently unnamed financial organization. When such calls come out of the blue, it’s generally best to either hang up or press the suspicious agent for confirming info.
4. Uncanny Identities
Even in our age of autocorrect, typos are fairly commonplace. The exception, however, is in official communications from companies, since an unprofessionally written message will reflect badly on their reputation.
So if you receive a text or email purportedly from a big, well-known entity that’s inexplicably full of spelling errors and obvious grammatical faults, there’s reason to doubt its authenticity.
As elitist as it may sound, be on the lookout for mistakes or other marks of unprofessional writing when you get an oddly urgent message out of the blue. That’s typically a sign that the sender is someone without an actual reputation to protect.
5. Avoid the Panic Button
One of the hallmarks of a successful scam is inducing alarm in victims. It should come as no surprise why: if a person is panicking, they’ll do nearly anything for the sake of personal security (even give their account info away to shady individuals).
In practical terms, this means if an email, text or call seems precision-designed to make you panic, it probably doesn’t have your best interests at heart.
Yes, a warning about your account being compromised is bound to set off alarm bells. But consider the phrasing of the message you got: Does it seem more intense than needed? Is it especially aggressive? Does it threaten consequences if you don’t follow up on its demands?
Any of those qualities generally mean the message isn’t there to give you actual information, but to put you in a state of emotional vulnerability — and that in turn signals that the message is likely a hoax.
Preparation Is the Best Defense
Although staying safe from phishing is largely dependent on individual users, the upside is you’ve already done a lot to defend yourself just by being aware of these scams. If you simply arm yourself with the knowledge that not every message-sender is who they appear to be, you’re already one step ahead of their plans.
The other thing to remember is that, although these aforementioned tips for identifying cases of phishing are consistently reliable, the specifics of each scam are always changing. Scammers regularly create new strategies for hoaxing the unaware, so it’s wise to keep your ear to the ground about any new tricks such con artists are now using.
This is all especially critical now, as cyberattackers — particularly those with resources supplied by the Russian government — remain rampant and even on the rise. In fact, cases where Russia-linked cyberattackers commit phishing show that these scams can do more than just cost your business funds and reputation — they can redirect company resources into efforts for actual warfare.
For yourself and even the world abroad, there’s never been a more important time to stay aware and keep your own systems protected.
For more tips on cybersecurity and tech, subscribe to receive our magazine for free!