Outside of paper cuts or mosquitoes, few subjects have earned as much universal scorn as robocalls — especially ones with fake caller IDs. These days, it’s often enough of an interruption simply to get a phone call. But to pick up a local or official number, only to hear yet another monotone text-to-speech scammer? That’s enough to peeve most anyone.
Odds are, you’ve already had the displeasure of picking up one of these “spoofed” calls, or calls with deliberately faked caller IDs. In 2022, the US alone was hit with 50.3 billion spam calls, a colossal number consistent with the worldwide highs of robocalling reached in 2019. And all too often, these calls worm their way in by tricking users into thinking what they’re picking up is a worthwhile message.
Fortunately, by now technology exists to help prevent those scammy calls. It’s a set of connection protocols called STIR/SHAKEN — yes, named in part after a certain espionage agent’s drink instructions. And this technology isn’t just useful; in the US and Canada, it’s required by law to be implemented on phone systems.
Wildix, of course, features full support for it, as STIR/SHAKEN can be easily made a part of any Wildix setup via CLASSOUND, the premier international voice service. And with just a bit of tweaking and know-how, it can be set up to stop spoofed numbers from coming into your PBX.
The Scoop on Spoofing
First, we should emphasize that STIR/SHAKEN doesn’t outright block all robocalls before you can even pick them up. Until we develop Minority Report levels of predictive technology, we shouldn’t expect any such breakthroughs in call screening.
What STIR/SHAKEN does accomplish, however, is better prevent call spoofing by adding new verification steps to the caller ID process.
The reason this is necessary at all is because caller ID is highly exploitable. Thanks to the way the system was designed, at no point does it confirm the number on your phone screen is accurate.
“It used to be that pretty much every single carrier didn’t care what you sent for a caller ID number or name,” says Jerry Browne, Wildix Support and Technical Assistance Manager. “They just took it and forwarded it along — nobody ever checked it or did anything with it they just used it they trusted it.”
Scammers, of course, have long been aware of this. Although there have always been spam factories calling from unknown numbers, most con artists recognize they’re more likely to reach their marks if they appear as someone known to their mark.
But even worse, spoofed numbers leave little trace for victims to follow up on. Because the caller ID number isn’t accurate, call recipients can’t accurately report the spammer or even dial the number back, effectively leaving them to disappear into the ether.
STIR/SHAKEN on the Scene
What STIR/SHAKEN brings to the table, then, is the critical step of verification. Using partly old, partly new technology, the protocol enhances caller ID with better safeguards against spoofing.
As the name implies, STIR/SHAKEN is made up of two components:
-
- STIR, short for Secure Telephony Identity Revisited, is a protocol for adding verified info about a calling party into the call’s digital signature. It is utilized mainly on end-devices, such as your phone or computer’s VoIP software.
- SHAKEN, short for Secure Handling of Asserted information using toKENs, implements the STIR protocol for carriers. It is utilized mainly over telephone networks to better direct validation processes.
Used together, STIR and SHAKEN initiate a process that compares an outgoing call’s ID to other known IDs for that customer, then attaches a definitive label to the call using a digital certificate.
That digital certificate is central to how STIR/SHAKEN becomes more effective than caller ID as is. Like with web security, the STIR certificate is encrypted — that is, masked using a one-time code — using the carrier’s own certification. This assures a receiving carrier that an incoming call was verified to the point it received a personal stamp of approval, putting providers on the hook to not let spoofed calls go through.
STIR/SHAKEN for Wildix, Step by Step
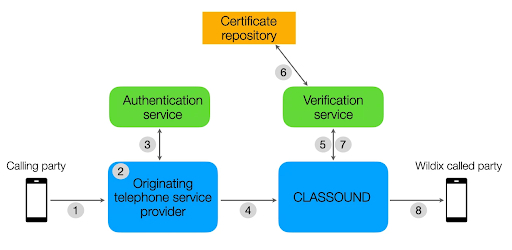
Listed out, the path that STIR/SHAKEN takes on a Wildix CLASSOUND system flows like this:
- SIP INVITE generation
The originating telephone service provider receives a SIP INVITE, a digital invitation asking the service to give more verification on the call. - Assign attestation level
That same originating provider verifies the call under one of three categories:- Full or A Attestation: The calling party is a number that’s authorized to use the calling number, like a subscriber registered with the provider’s softswitch.
- Partial or B Attestation: The call origination is authenticated, but it’s not clear if the caller is authorized to use the number, like a telephone extension for a PBX.
- Gateway or C Attestation: The provider can determine where the call was but cannot authenticate the call source, like a call received from an international gateway.
- Generate a SIP identity header
Next, the service provider uses an authentication service, such as integrated software or a cloud solution, to create a SIP Identity header. This header is digitally encrypted and contains data like attestation level, calling number, the origination identifier and a timestamp. - Reception
The SIP INVITE is sent to CLASSOUND, where the SIP Identity header is decrypted. Now, CLASSOUND has assurance from the originating carrier that the call was not spoofed. - Initiate verification
Even so, we want to be certain for ourselves, not just take the carrier’s word for it. To do so, CLASSOUND sends the SIP INVITE and its Identity header to its own verification service. - Verify the number
That verification service then matches the digital certificate included in the Identity header against what’s available from the public certificate repository. The service verifies the call has not been spoofed if all of the following verification steps are successful:- The SIP Identity header is base64 URL decoded and the details are compared to the SIP INVITE message
- The public key of the certificate is used to verify the SIP Identity header signature
- The certificate chain of trust is verified
- Results are returned
The verification service sends the results back to CLASSOUND. - Completion
CLASSOUND accepts the results and the call is completed.
Visual representation of the STIR/SHAKEN process.
With these steps in place, calls received by CLASSOUND are far and away less likely to be spoofed.
The Limits of STIR/SHAKEN
All this being said, STIR/SHAKEN won’t on its own slay the hydra-like menace of robocalls.
To reiterate, it’s impossible to block all spam calls with current technology. The big advantage STIR/SHAKEN brings to the table is that it more consistently forces callers to use their actual caller ID in place of a spoofed one. What STIR/SHAKEN cannot do, however, is block a spam call that displays its actual dialing number.
“At the end of the day, people are still gonna spam crap, and you’ll always get calls from a spam number that you can’t dial back,” Jerry Browne points out.
“Why? Because if I, as a company, buy a block of 1,000 DIDs, I can make only a couple of those actual numbers that come into my system, then make the other 998 not route to anything. Then if someone calls me back from one of those 998 bad numbers, the carrier just won’t complete the call.”
The good news is we can still expect numbers that are consistently reported for spam to be initially blocked by carriers. And when networks use STIR/SHAKEN, we have far more of a guarantee that the number displayed on a spam call actually is the number being dialed out from.
There are also plenty of ways engineers can improve STIR/SHAKEN, especially with a system as flexible as Wildix.
“Let’s say you’re sitting on a number from another carrier, and you want to port it to CLASSOUND,” Jerry explains. “Even though you don’t have that number ported yet, right away you can whitelist it as a good caller ID number and allow it to make calls.”
Although the full effects of STIR/SHAKEN are yet to be seen, for now it serves as an effective way to block the most obvious of spam calls. And given just how many scams are still clogging phone lines, it’s safe to say every little bit will help.
Check out STIR/SHAKEN in greater detail, including instructions on how to implement it yourself (US and Canada only), on the Wildix Confluence page.
For more tips on telecommunications technology, subscribe to receive our magazine for free!